One of the many quirks of quantum mechanics is that unknown quantum states can’t be copied, which presents major challenges for both quantum computing and quantum communications. Now, researchers have shown they can bypass this restriction by encrypting qubits as they clone them, which could provide powerful new capabilities including a quantum equivalent of cloud storage.
Much of the power behind quantum technologies lies in the fact that qubits–the quantum equivalent of bits–can exist in a superposition of many possible states until they are measured. This allows quantum systems to represent and manipulate many possibilities at once, unlike classical bits which are always either 0 or 1. However, measuring a qubit causes its superposition to collapse into a single, definite state. This makes it impossible to create a copy of the qubit, as to replicate it one would first need to measure it, which would unavoidably disturb the state being copied.
This fundamental barrier is known as the “no-cloning theorem” and presents both advantages and disadvantages for quantum technologies. It’s the reason why quantum communication systems are so secure–anyone attempting to intercept a quantum signal cannot read it without altering its state, making it obvious that the message has been compromised.
However, it also means it is impossible to create copies or backups of qubits, which prevents quantum technologies from replicating fundamental techniques used in classical computing and communications. For instance, cloud providers typically create many copies of a customer’s data and store them in several different locations to create redundancy, and digital communication systems protect against data transmission errors by sending multiple copies of a message. Now though, a pair of researchers have discovered a deceptively simple workaround.
“In classical computing, copy and paste and making backups is done all the time, everywhere, and it appeared as if in quantum computing we just have to forget about it,” says Achim Kempf, a professor of applied mathematics at the University of Waterloo in Canada. “What we found was that qubits can, in fact, be perfectly cloned under one condition. While you clone them, you also have to encrypt them.”
A serendipitous discovery
Kempf says he and his collaborator Koji Yamaguchi, an assistant professor at Kyushu University in Japan, stumbled across the discovery while Yamaguchi was working as a post-doctoral researcher in his lab. The pair were investigating the possibility of wireless quantum communication and how this would be impacted by random quantum fluctuations inherent to all electromagnetic fields. In the process, they discovered that adding noise to a qubit could essentially encrypt it so that its state can’t be measured until it is decrypted by subtracting the noise again.
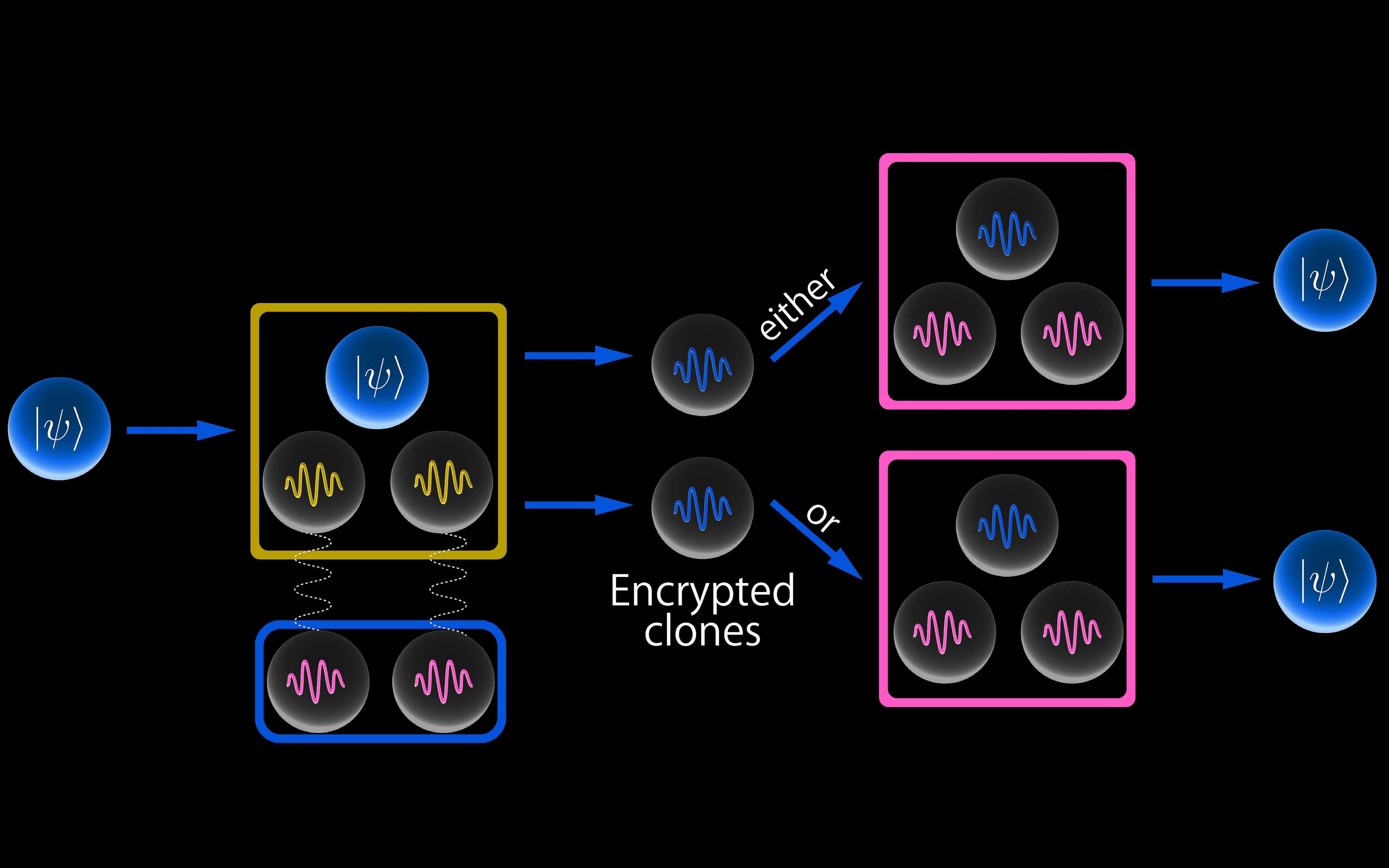 Encrypted cloning represents a new paradigm that provides a form of redundancy, parallelism, or scalability where direct duplication is forbidden by the no-cloning theorem. For example, a possible application of encrypted cloning is to enable encrypted quantum multi-cloud storage.Koji Yamaguchi and Achim Kempf
Encrypted cloning represents a new paradigm that provides a form of redundancy, parallelism, or scalability where direct duplication is forbidden by the no-cloning theorem. For example, a possible application of encrypted cloning is to enable encrypted quantum multi-cloud storage.Koji Yamaguchi and Achim Kempf
They also found that it was possible to create multiple encrypted copies of the qubit, because the quantum state remains hidden until one of the copies is decrypted. The scheme, which is detailed in a recent paper in Physical Review Letters, works in much the same way as a classical “one-time pad”, says Kempf, where a message is encrypted by combining it with a key made of a string of random numbers using a special arithmetic operation. To decrypt the message the receiver has to use the same key to reverse the operation.
Crucially though, the key in the new quantum encryption scheme only works once, says Kempf, which means it’s only possible to decrypt one of the copies. This is essential for ensuring that the approach doesn’t fall afoul of the no-cloning theorem, because it means that you can never observe the state of more than one of the clones. “There only ever can be one clear copy of the quantum information, that’s mandated by a law of nature,” says Kempf.
The quantum encryption scheme works by first generating pairs of noisy entangled qubits. These are split into signal qubits used to create clones and noise qubits that keep a record of the noise on the signal qubits, which essentially acts as the scheme’s “encryption key”. A quantum circuit then makes the qubit to be copied and the signal qubits interact, causing its quantum state to become imprinted on the noisy signal qubits.
To read the state of one of these “encrypted” signal qubits you first need to subtract the noise from it. This is accomplished by another quantum circuit that makes one of the signal qubits interact with all of the noise qubits, cancelling out the noise and making it possible to read the quantum information copied from the source qubit. This interaction also causes the state of the noise qubits to change, which is why the key can only be used once.
There have been previous attempts to bypass the no-cloning theorem, says Yamaguchi. However, other quantum cloning protocols can produce only approximate copies, he says, and the more you make the more the quality of the copies declines. In contrast, the new approach can, in theory at least, generate an unlimited number of perfect copies.
The practical potential
Mark Hillery, a professor of physics at City University of New York who specializes in quantum information, questions whether the approach truly counts as cloning, as only one qubit ends up in the same state as the initial qubit and no additional copies are produced. Nonetheless, he thinks the protocol could prove useful for quantum communication. “Teleportation can transfer quantum information from one qubit to another, but this new protocol adds several novel elements,” he says. “First, the quantum information can end up in one of many different qubits, and second, unlike in teleportation, no classical communication or correction operations are required. It is a very nice result.”
The researchers have also already tested out the scheme on real world devices. In unpublished research conducted with colleagues at IBM, they validated the new encryption scheme on the company’s Heron processor, demonstrating the ability to generate large numbers of encrypted clones. Kempf says the experiments showed the approach is not overly sensitive to hardware imperfections that can derail quantum operations. And crucially, they demonstrated that clones not only replicate the original quantum state but also remain entangled with any other qubits that the source qubit was linked to. “The experiments turned out really beautiful and better than we could have hoped,” says Kempf. “The encrypted cloning protocol not only works, but it works quite well.”
The researchers say the approach means it is now possible to add redundancy to quantum information systems. This could enable a quantum equivalent to cloud storage, where multiple copies of quantum data could be stored in different locations. It could also make quantum communication and sensing more robust by transmitting signals as a stream of encrypted qubits rather than a single qubit that can be easily disrupted.
More ambitiously, the pair now hope to devise ways to carry out computations on the encrypted qubits. Carrying out computations on data you cannot read carries significant overheads, admits Kempf, but could enable powerful new capabilities. “You can imagine a quantum cloud service provider would be able to provide not only safe redundant storage of your quantum data, but also safe redundant computation on your quantum data,” he says.
From Your Site Articles
Related Articles Around the Web
🎯 Top1Go : LINK TO THIS BRAND SUPPLIER
#Encrypted #Qubits #Defy #Cloning #Limits, quantum computing, quantum communications, quantum sensor, encryption ,




![Encrypted Qubits Defy No Cloning Limits[🤖🇺🇸]](https://top1brand.top1index-top1list.com/wp-content/themes/rehub-theme/images/default/noimage_500_500.png)
![Encrypted Qubits Defy No Cloning Limits[🤖🇺🇸]](https://top1brand.top1index-top1list.com/wp-content/themes/rehub-theme/images/default/noimage_70_70.png)
![Insane Climb | INTO THE DEEP | FTC 17077 Robot #intothedeep #firsttechchallenge [🤖]](https://top1brand.top1index-top1list.com/wp-content/themes/rehub-theme/images/default/noimage_336_220.png)
